Unplug Then Plug Back in It Starts Again Mobile Forensics
A mobile device is a goldmine of information; in an era where 98% of investigations involve some form of digital testify and information volumes continue to grow exponentially, having the most advanced mobile forensic tools at your disposal – from the get-go extraction, to analysis, to management and eventually, in court – is critical. Just with dwindling resources, time, and the ongoing challenges impacting today's law enforcement operations, how does your agency go along up in a forensically-sound, efficient manner now and heading into the future?
Bring together usa for an exploration of how MSAB'southward complete mobile forensic ecosystem can dramatically scale upwards your forensic operations while automating and simplifying your workflow. In this session, we'll look at means examiners, managers, investigators, and analysts tin can harness the power of MSAB's mobile forensic tools to reduce the evidentiary backlog and automate device extractions inside of our powerful XRY, XAMN, and XEC solutions.
Transcript
Kevin: Thank you for joining this MSAB presentation on the time to come of integrated forensics: ecosystem solutions for digital forensics investigations.

My proper noun is Kevin Kyono. I'm a technical sales engineer with MSAB. I've been with the company for virtually a year and a half and joined them after a 27 year career with the San Jose police department. Well, allow the SJPD, I was in the detective agency for eight years. During those 8 years, I performed digital forensics in the high-tech crimes unit of measurement for five years and was as well the forensics team leader in the Silicon Valley ICAC task force for three years.
The last year and a half earlier I retired, I was also the ESD canine handler for the task force. The ESD canines are the dogs that can locate mobile devices, like cell phones, hard drives, pollex drives, and even the smallest SD cards. That's my girl, Heidi, on the screen. And thankfully she was able to retire with me.
Then merely to provide a lilliputian background on the visitor, MSAB is a Swedish based company which specializes in mobile forensics. We produce a suite of products designed to extract and analyze the data from mobile devices. Our products are deployed in over a hundred countries beyond the world, and we sell primarily to government and law enforcement agencies, and to a very pocket-sized number of vetted individual companies. We will never sell to companies supporting defence attorneys, or to unscrupulous countries. Whereas our largest competitor will sell to anyone who will pay them. Yous will never see our products in the hands of the bad guys.
As you know, the use of mobile devices is increasing exponentially every year. It's estimated that in the year 2020, over 51 exabytes of data were transmitted per calendar month over wireless networks. That's the equivalent of 51 billion gigabytes of information per month. Coinciding with gild'southward increased usage of mobile devices, crooks are as well increasing their use of mobile devices to commit crimes or are in possession of their devices while committing crimes.

Our ecosystem of tools will help everyone from the frontline user to the administrator. We will help the frontline user chop-chop and hands find their actionable intelligence in a forensically sound manner that will agree upwardly in any court of law. And we'll also help the administrators manage that ecosystem, from gathering statistics to keeping the entire deployment up to date. There are other products out there that tin can also perform forensics on mobile devices, simply I'm going to show you what sets us apart from the residual.
MSAB has multiple tools to assist you, but our primary ones are XRY, XAMN and XEC. XRY is used to extract the information from devices; XAMN is used to analyze that data; and XEC is there to assistance you manage your ecosystem. I'thousand going to give you a high level overview of our tools and how they tin help your bureau.
XRY is our mobile device extraction tool. So we tin can extract cell phones, tablets, drones, and even portable storage devices similar SD cards. At present allow's show yous a live demo of XRY'south features.
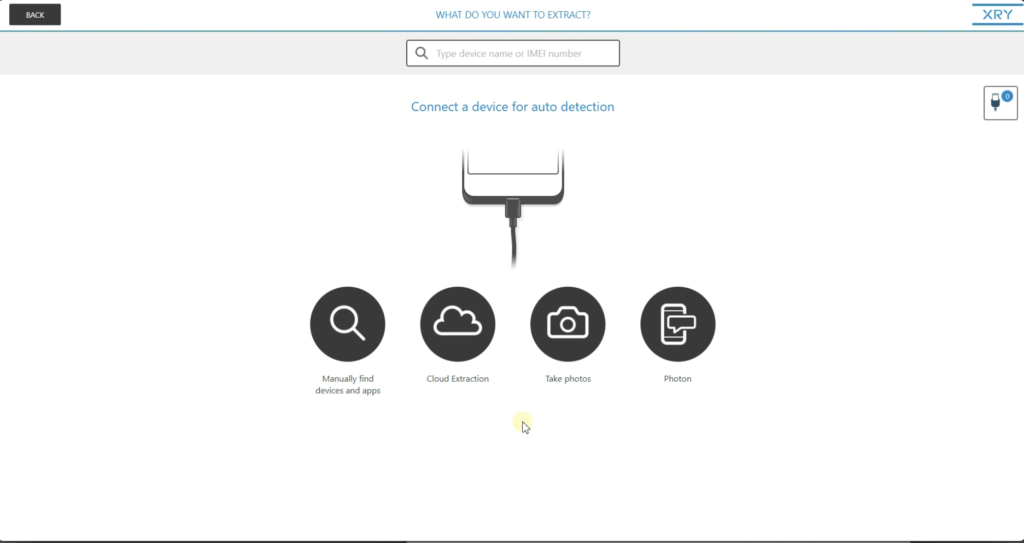
So what yous meet here is the splash screen for XRY. You can see how unproblematic the user interface is. The master thing hither is where you could connect to the device for other detection, you lot can manually search for a device or an app. You could do a cloud extraction, take photos or use Photon. And we'll talk about Photon in more item in a fiddling chip here.
What I'm going to practice hither is search for a device manually, by clicking here in the text box. Yous come across by this listing, we support over 34,000 different devices. If I click on Apps, we take support for over 400 apps.
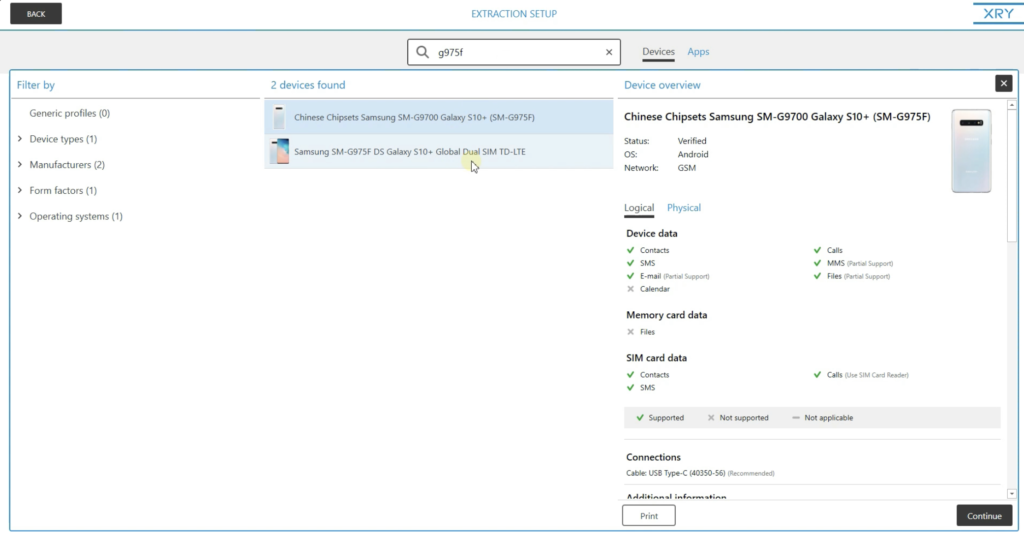
XRY also has back up for thousands of locked devices. We have the power to either brute force the passcode or completely bypass the passcode. So if I go back to the devices, if information technology start typing out a model number of a phone that I know we accept total back up for — if I kickoff typing G975F — yous'll meet it belongs to a Samsung Falaxy S10+, which is one of the newer Samsung phones. If I click on that device, and I click on concrete, you'll see the clarification it says 'design lock can be bypass regardless if USB debugging is enabled or not.' So what that's telling me is that nosotros can bypass this passcode and extract the data out of it.
XRY can also perform cloud extractions. So if I get back to our splash scree, you'll see we take our deject extraction button here. Click that. You'll notice that all major providers of deject data are supported hither, from Apple tree and Google to Facebook and Snapchat. All the major players are here.
If you lot know the username and countersign, you can manually extract the data, or it'south also possible to automatically extract unabridged deject accounts without even knowing the user business relationship name and password past using credentials XRY locates during your device extractions. But the virtually common task yous're going to perform is a device extraction.
And then let's go back to our splash screen. I'grand going to plug in an Android device and let XRY automatically detect it. See how quickly it identifies an Android device. Now it's going to go to our extraction set upwardly page. On the left column hither, you're going to see a tab that says pre scan data. If I click pre browse data, we're going to be able to triage the device for identifying information and install that. And this is all pre extraction.
So you'll see the manufacturer, the model proper name, serial number, what version of the operating system it's running, as well as how much storage is beingness used. And so it gives you lot a judge on how much data is within that device. Simply very chiefly, you'll see a list of known apps. So these are all the apps that are installed on the device.
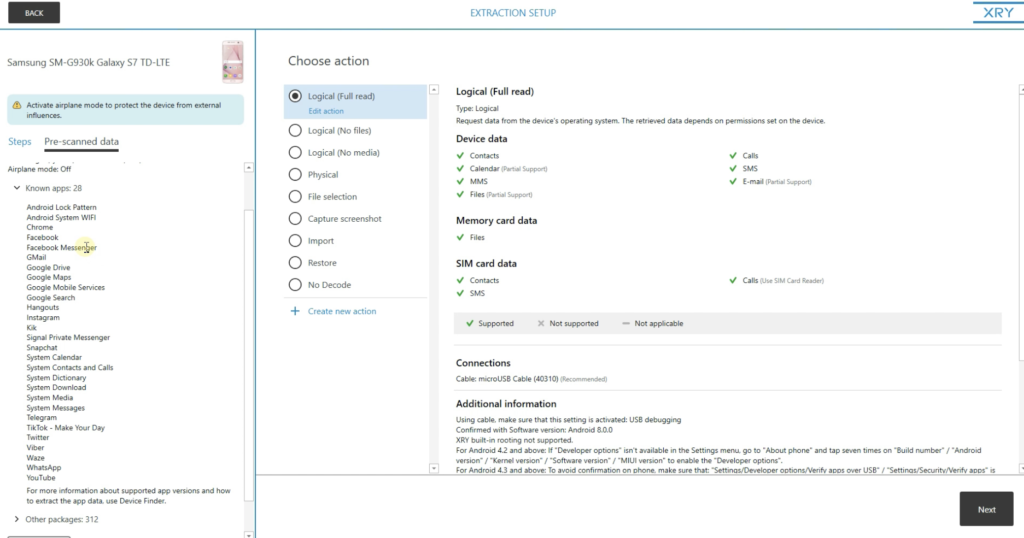
So this tin be very important in triaging your case, especially if you have a stack of devices in front of yous. Say for case, the case yous're working is a Snapchat case or WhatsApp instance. Yous can look through this list and if you don't meet Snapchat or WhatsApp on your list, you may want to put that device aside and move on to the next device then you're not wasting a lot of fourth dimension. This tin quickly assistance y'all pinpoint what your primary device is going to be.
In the heart column here, you're going to see a list of tasks you tin perform with this device. The most mutual are going to be a logical extraction and a physical extraction. So I like to use a law enforcement illustration when comparing logical to physical extractions. And so your logical extraction is going to be like your knock and talk, or consensual run across. You're but going to get as much information out of that device as the operating organization is going to allow you lot to take. In near cases it's just about everything. Whereas your physical extraction is like a search warrant at a residence. You interruption down the door and everything in the house is available to you. Everything is fair game. A physical extraction is going to everything off of that device.
I'thou going to select logical, click side by side. And so this next screen, you come across the timespan customization folio. You can specify the exact timespan for your extraction. You lot can select all, which will give y'all everything. You can select the last year, last 30 days, 7 days, the last 24-hour interval, or you lot can do a complete custom timespan. You can completely customize the verbal starting date and time to the cease date and time of your extraction.
This is nice because it can help you stay within the legal boundaries of the warrant. The courts are getting very restrictive, especially here in California. And this feature tin assistance yous stay in a hundred percent compliance of that legal order. And this is a feature that's exclusive to XRY. You will not meet this feature in whatever other tool.
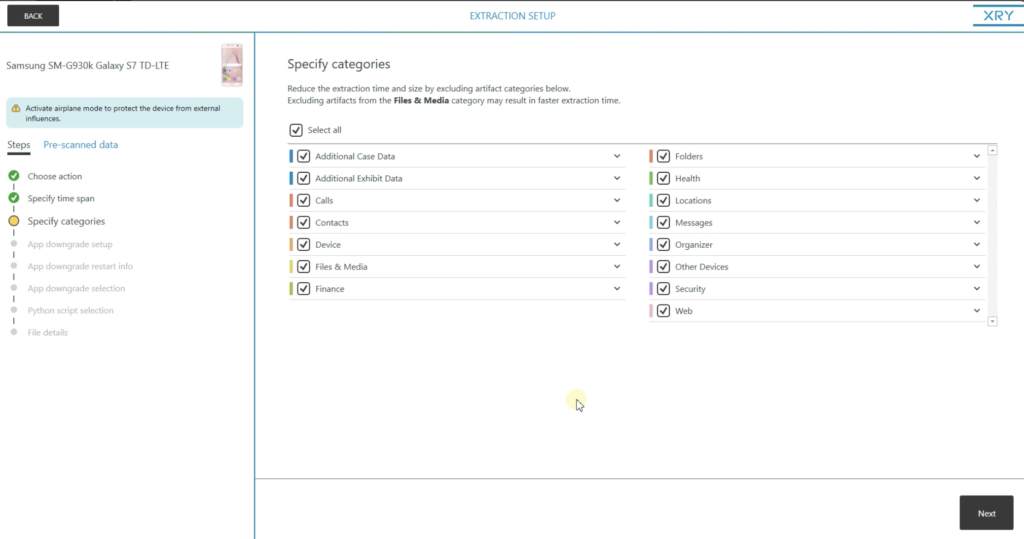
I'll click side by side. And so we can come up to our file category customization. Then from this screen, you can customize what file categories you want to include in your extraction. Then if you're only looking for pictures, yous tin just select pictures. Or if you're looking for pictures and videos, you could just select pictures and videos. There's a vast array of customizations you can do here. And not only will this save you time on the extraction, but it volition relieve you time on your assay also, considering yous're simply pulling out the data that you need for your case.
Okay, we'll click next. And and so at the next screen, we take our app downgrade page. So we accept the ability to downgrade apps to previous versions. Then as you're well enlightened, apps are constantly getting updated, y'all know, sometimes every calendar week, every 2 weeks, and it's kind of a catch-up game for our developers. So nosotros have the ability to downgrade apps. And so if you do an extraction and you're non getting the data that you lot know should be there, you tin can downgrade the app. And so what we'll practise is we'll downgrade the app to the latest version that we do support, extract the data, and so re-install the original version dorsum onto the person's phone. And then we're non irresolute whatsoever user created data. Nosotros're just extracting that data that nosotros exercise need. And then everything volition still exist extracted in a forensically sound manner.
Nosotros're going to select downgrade none, click next. This next page is more for avant-garde users. We have the ability to import Python scripts and run them during the extraction, but we're not going to get into that at all. That'south more for the high end users. So nosotros'll click next.
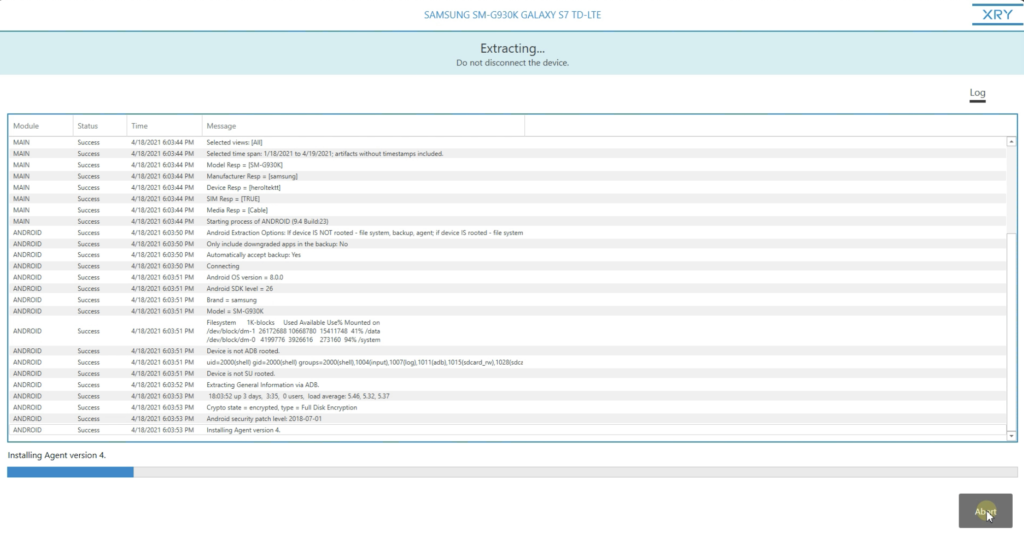
Nosotros enter our device details and our user info, and so click next. And at present yous're going to come across our extraction log. And then we do a total inspect log for transparency in what is taking identify during the extraction. So everything is there. Every procedure that's done on the device is going to be documented. Then not only is this proficient for potential court purposes, you know, if you have a[due north] overzealous defense attorney who wants to try and shake you a little bit on the stand up, just information technology's also practiced for customer service too, as far equally if you run into any problems, yous can give information technology to our customer support department. And they'll exist able to troubleshoot your log and discover out why you may not have gotten a good extraction on your device.
And then while this device is extracting, I tin can open up some other XRY page and commencement another extraction. So information technology could be another device from the same case, or it could be another completely dissimilar case. It doesn't matter. I can actually do 3 devices at once. And what'southward nice is that there'southward no chance of the evidence being cross-contaminated, and in that location's no degradation in figurer performance. What'due south prissy almost this, it'due south a huge time-saver. Peculiarly if you have multiple devices in front end of you lot that you have to hurry up and get extracted. And once again, this is some other XRY exclusive that you won't see with any other tool.
Another XRY exclusive feature that I want to testify you is called Photon. Then Photon is a screen capturing tool, especially useful for obtaining data from encrypted apps, only it tin also exist useful for just virtually any app. And then I run into now many communication apps now have stop to terminate encryption, and your regular extraction of the device isn't going to get that data. And the most popular encrypted apps nowadays are WhatsApp, Bespeak and Telegram.
So Photon volition obtain this encrypted data. So I'thousand just going to run y'all through the Photon process really quickly here. And so I'm going to click Photon, I'm going to click side by side, click next, I would enter my device information hither, click next. The device is connected, and it already recognizes the device I've connected.
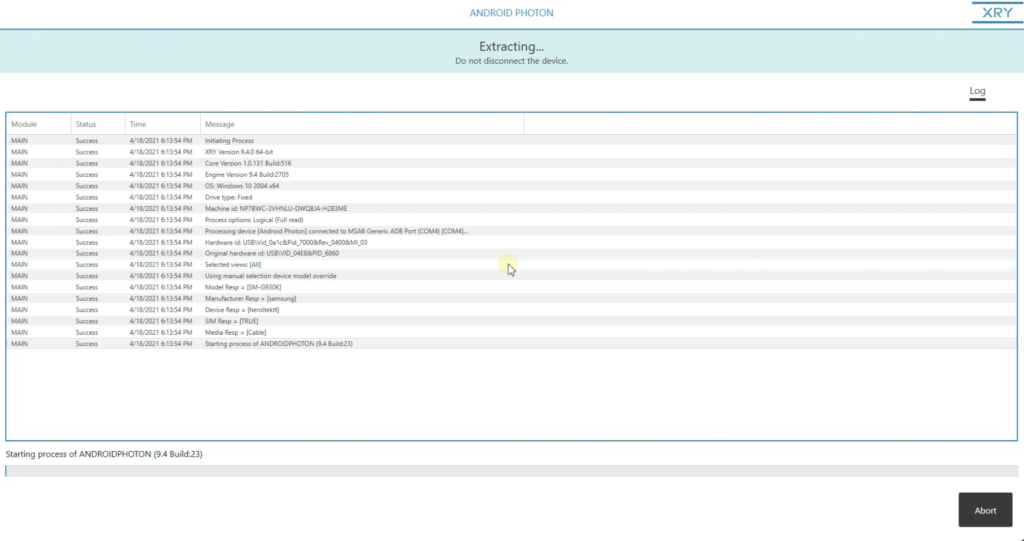
I'm going to select WhatsApp. I'k going to do a full contact extraction. I have the power to customize the date range, but I'm going to select all. I'thousand going to select all the messages, all the calls. And in a 2d here, it's going to come up with a list of all the contacts within my WhatsApp account. And so you accept the ability to customize a specific conversation, or you can select a couple of them, or you can select all of them. So select all.
Now, I'yard going to share my device screen with yous. This is the screen of my actual device, and I'm not manipulating it or touching it in any way. Then XRY's Photon has taken command of my phone and is now capturing screenshots of everything within my WhatsApp business relationship. And so it'south going to collect all my contacts, all my chats, dates and times are preserved. So everything's going to be nerveless here and it's going to brand everything very readable and searchable within XAMN, when we go to XAMN.
One last feature I'd like to encompass about XRY is file selection. File choice volition allow y'all to quickly extract photos and videos and audio files from a device in a forensically sound manner without doing a complete device extraction. Then this can exist very useful when you accept a reluctant victim, or a witness who doesn't desire to give up their telephone, and you can finish in a affair of minutes and return the phone that same mean solar day.
So this was very useful when I was in ICAC and we were dealing with teenage victims. As you all know, a teenager's entire life revolves around their telephone, and they can't conduct to exist separated from it. Then this can be a prissy solution for that. Just information technology can besides be used in major incidents where perhaps multiple people have recorded the incident. Perchance information technology'due south a workplace blow or some sort of major catastrophe where dozens, or possibly even hundreds of people recorded the incident. You lot tin can gather all of the devices, extract the video footage, and return the phones in a thing of minutes.
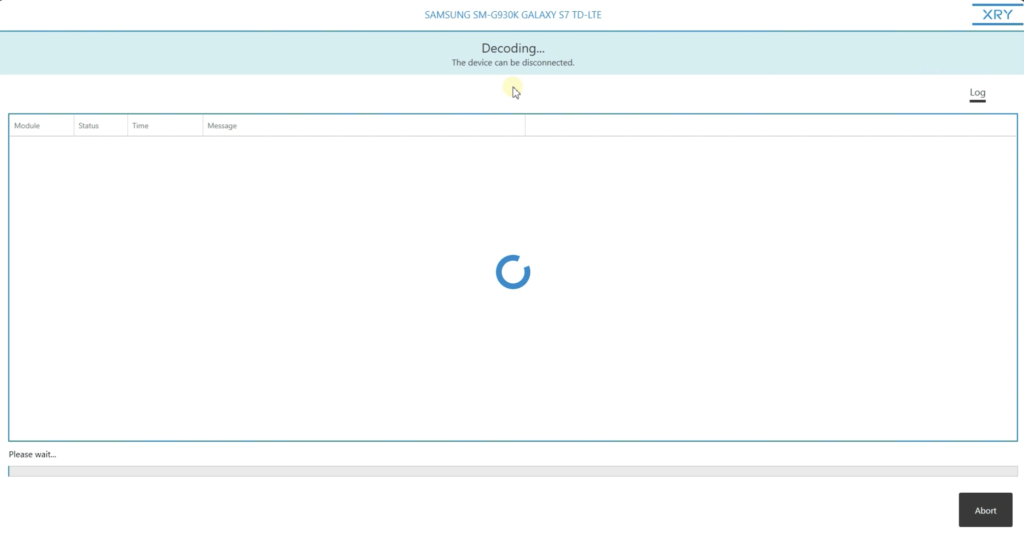
So I'm going to run you through a sit-in of that to evidence you how apace information technology can be done. I'k going to plug in my device. I'thousand going to select file pick. Click next. I'm going to access the folder where the videos are stored, which is in the DCIM binder. I'm going to select a video.
So say this is the video yous're looking for. I could select this file, go to my selected files. This is the file I selected, click next, enter my evidence information, click next, you meet up at the meridian of the screen that says 'decoding… device tin be asunder.' So just every bit quickly as that, I will unplug my device, hand it back to the possessor. They're happy because they have their device back, and I'm happy because I take the testify I need for my case.
Each time I create an extraction, whether it'due south a device extraction or Photon or file selection, whatever it may be, it creates a unmarried file with a .XRY file extension. What's nice virtually this file is that it is a hundred percent forensically sound. You tin can go to courtroom and say with a hundred percent certainty, that file has not been changed from the time you created the extraction to the time you did your analysis.
Information technology'southward because this file is fully hashed. It'south encrypted. And it's also compressed, which is nice for storage savings. If you make a change to this file — say you use some sort of editing software and make a alter to just one fleck of information — it's going to make that file where y'all can never open it again.
Our competitors, their files are not forensically sound, and potentially their prove can exist altered. Our evidence, there is zero chance of any alterations being made to our file structure.
Okay, permit's motion over to XAMN. Every bit I mentioned earlier, XAMN is our analysis tool used to view the information we extracted with XRY. It tin be equally elementary or every bit complex every bit you want it to be. The interface is simple for less experienced users, merely in that location are also advanced features for experienced forensic examiners.
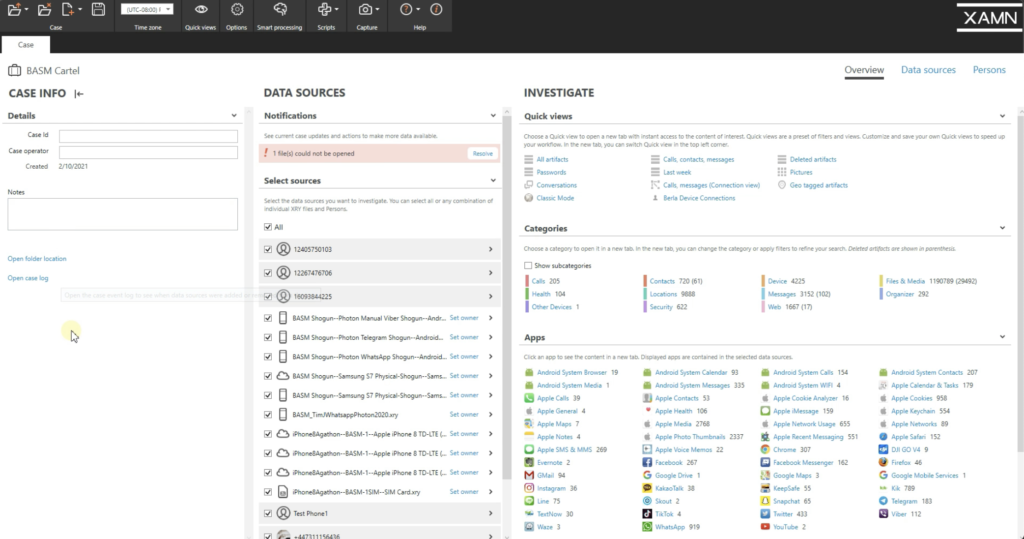
You lot're now looking at the homepage of XAMN. So this is what a typical case may wait similar. You lot have your case info on the left. You lot can customize these fields any fashion you similar. Afterwards you fill up in the fields, you tin can minimize that. Now you take your data sources. And so these are all split extractions here, and it could be a device extraction, information technology could be call information records from a cell phone provider, it could be a drone extraction. Information technology tin can be multiple types of evidence here, and those are all going to be listed here.
You also have notifications upwards at the top. And so you lot notice I have a notification there. So if I click resolve, it says an unknown mistake occurred when opening this extraction. If I click on it, check integrity, you'll see information technology has a bad CRC. So what this tin can mean is that this file has changed from the time I extracted the device. So as y'all can see, I'thou unable to open that detail extraction, which is what I explained before: these files are forensically sound. And if at that place are whatever changes that have been fabricated to the file, you tin no longer open information technology.
Go back to my overview. And then you have your investigative column. Then in this column, you could quickly leap to any of these categories of evidence. So you've jumped to pictures, conversations, calls, or messages. You accept calls, locations, web history, simply a vast array of categories. Or yous could spring to any of the artifacts from apps that are installed on these devices.
In the categories, I can also show sub categories. If I click sub categories, you'll see that opens up even more categories here, where I can really narrow downward what evidence I want to look at.
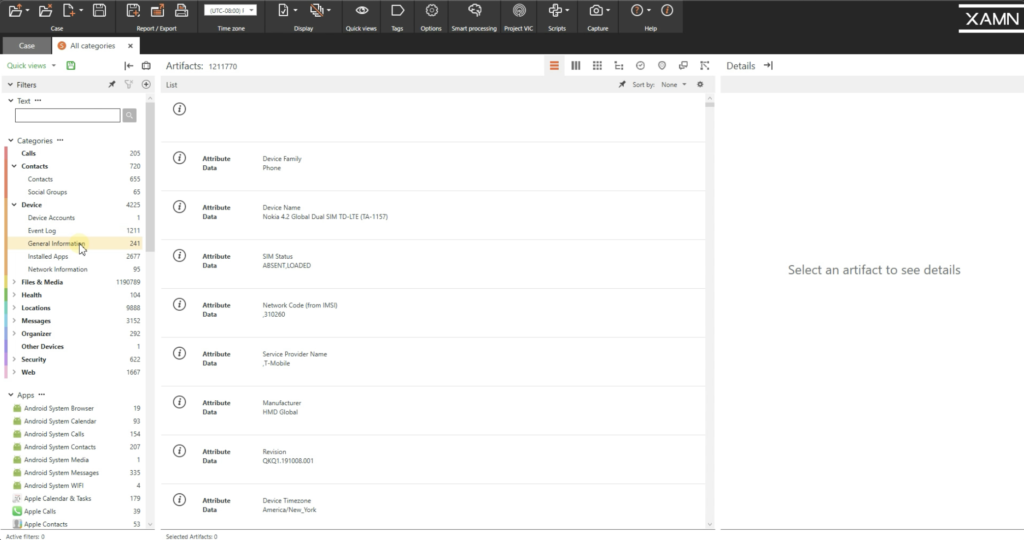
But normally I will click all artifacts, which will show all of my information all in one place. So now that nosotros take all of our artifacts open up, we tin now actually dig deep into what data is stored on all of these devices. On the left side here, you lot run across we accept all of our principal filters. These are default filters. We have calls, contacts, so I could open up contacts for even subcategories, devices — so you have all your device info — installed apps on these devices. Files and media are going to include your pictures, videos, audio files, documents. And then y'all see here, we accept over 500,000 pictures that were extracted. Y'all have health information. And so if these people are using any of these wellness apps, nosotros can plot all that information. Locations may be big for your cases. If there's location history, nosotros can pull that up, look at it in map view, and you can see pinpoints on where artifacts are.
And if I only roll my cursor over it, y'all could encounter what the antiquity is: messages. So it could be chat messages from maybe Facebook messenger, emails, text messages. If I open up upwardly the text messages here, open information technology in conversation view, and then y'all can see all the prissy little chat bubbles. I'll open up 1 of the conversations, and you see hither, we have our nice little to and from chats, people talking back and forth.
Y'all see here, one of them is fifty-fifty in a foreign language. It looks like French. If I click on the message and look at the details pane, I tin can highlight that text, click interpret only this, it'll open up a translation window and then will interpret that for me in a matter of seconds.
Going downwards a lot further, nosotros have security. So this could exist business relationship information here. Yous see accounts here for Viber, WhatsApp, Facebook. So if I just click on Facebook, for example, you see all the account information for this person, a name, birth engagement, email address, telephone number.
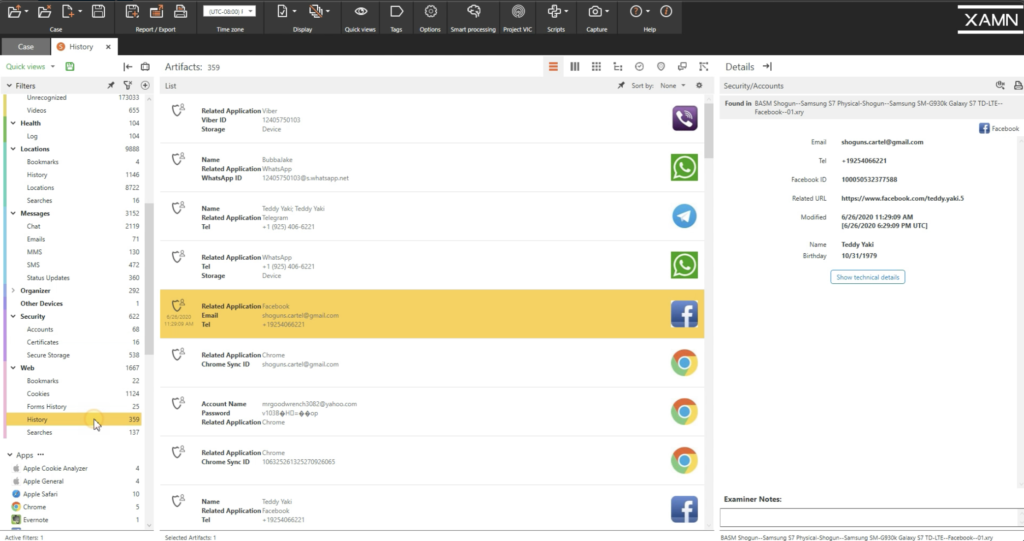
We accept spider web history. We have your bookmarks, cookies, bodily websites that these people have visited, and it could be a large one hither, is Google searches. And so yous've look at these searches here, how to sell guns, automatic weapons, prostitution laws. These can be all critical for your case here.
And scrolling downwards a piffling further, a big one hither is deleted artifacts. So I'm hoping yous all know that deleted doesn't necessarily mean deleted. So there could be a vast amount of valuable data here in your deleted artifacts. Like, we have pictures of a burglarize, picture of a shotgun hither, pistol, we have some location photos. These are all… technically they're deleted, but these artifacts are nonetheless inside of these devices.
Now I'm going to show you the results of the Photon extraction I did with XRY. So if I select this trivial suitcase up here, it shows that I accept multiple items of evidence open. Currently I could de-select them all. And I could just select my WhatsApp extraction.
And so you see here, these are all the screenshots that were captured with Photon. These are all the chat messages within Photon — or within the WhatsApp business relationship and captured by Photon — and Photon likewise pieces together the entire chat. So if it's a long conversation thread, Photon will slice it all together into one long string, which tin be very nice for presentation purposes, especially if yous're going to court. The juries love to see these actual chat messages.
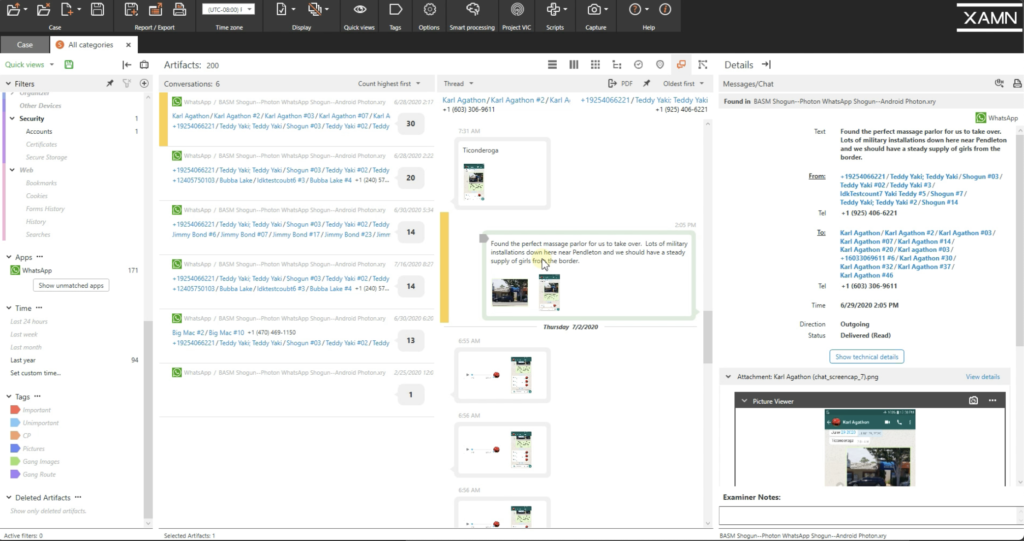
Just yous tin also look at information technology in conversation view. So all of these conversations are now indexed as well. So all of the text from inside these screenshots has been captured, and now you can see exactly what all that text was. And if there were images embedded with the message, information technology too captures that image.
And all this text is searchable likewise. So if you know some keywords yous're looking for, you could just type them up here in this fiddling text search box and information technology will notice that for you. Then I come across the word bandit. If I merely start typing the word bandit, you see it populates automatically for me right here. If I click it, information technology's going to pull upwards all the letters that have the word bandit in information technology.
So all of these messages that were pulled out of WhatsApp had been encrypted, but Photon worked effectually that and extracted everything out of the account.
XAMN tin also help you lot make clean up your case and make connections between the individuals. So if I close this out here, I'm going to click on persons, from our main case overview folio, and say your main suspect, you know what his proper name is. Say his proper name is Teddy. If I type Teddy, you'll see that XAMN has already identified multiple instances of this person. Maybe Teddy Yaki is your suspect'southward proper noun, it's already found multiple instances of his identity within these devices.
So if I click this main i here, it'southward showing Teddy Yaki is here with a proper name, a phone number and a Telegram ID. XAMN has automatically done that for me. Simply it's also identified artifacts that thanks may belong to Teddy, but it isn't quite sure. And then I can go through and manually make these connections and accept it included in my case.
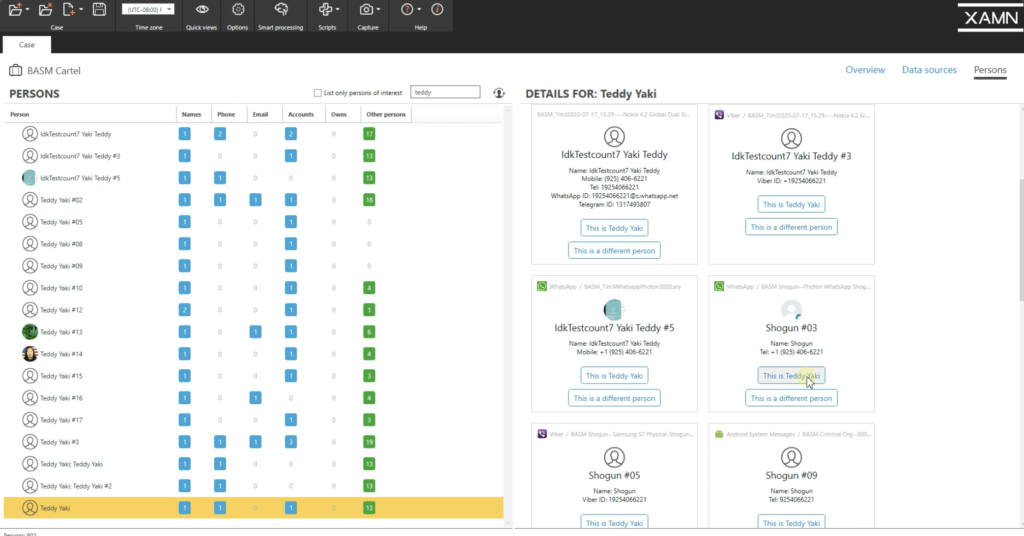
Then if I say, yes, this is Teddy Yaki. I see here, this one, this says Shogun. So I now have a nickname for this person. Maybe I didn't know this nickname before, but I accept the same phone number identified with it. And then I can say, yes, that'due south Teddy Yaki. So now I have another name associated to him upward here, Shogun.
So I could continue going down through this and find more connections. You see this 1 here is a big connection because it has multiple identifiers: phone numbers, email addresses, WhatsApp IDs, I tin say, yes, that'southward Teddy Yaki. And at present await up the height here. I accept all these connections here. I become information technology his nick ame, if I have to, and I can even add an image to it, say, this is my primary suspect. I could now listing him equally a person of interest.
Say my other suspect'due south name is Big Mac. That'due south all I know him by. I don't know his real name, but I typed Big Mac. So at present I type Big Mac. I see multiple instances of Big Mac here. So if I just look at the master one, I have Big Mac and a WhatsApp ID. But every bit I go down, XAMN has already identified people that it thinks may be Big Mac. So now I peradventure have his first name and last initial here, because this is the same identifiers here. I tin say, yes, this is Big Mac.
Looking up here now, I have Big Mac and a possible proper name of Adam D. So later I added that Adam D, I now have another business relationship here that it thinks might exist associated. I now have a last proper noun, Adam Dale. I can say, yes, that's Big Mac. Now I take multiple identifiers here. I can at present list him equally another person of interest. So from this large list here, at present, if I need to, I can just show persons of interest only.
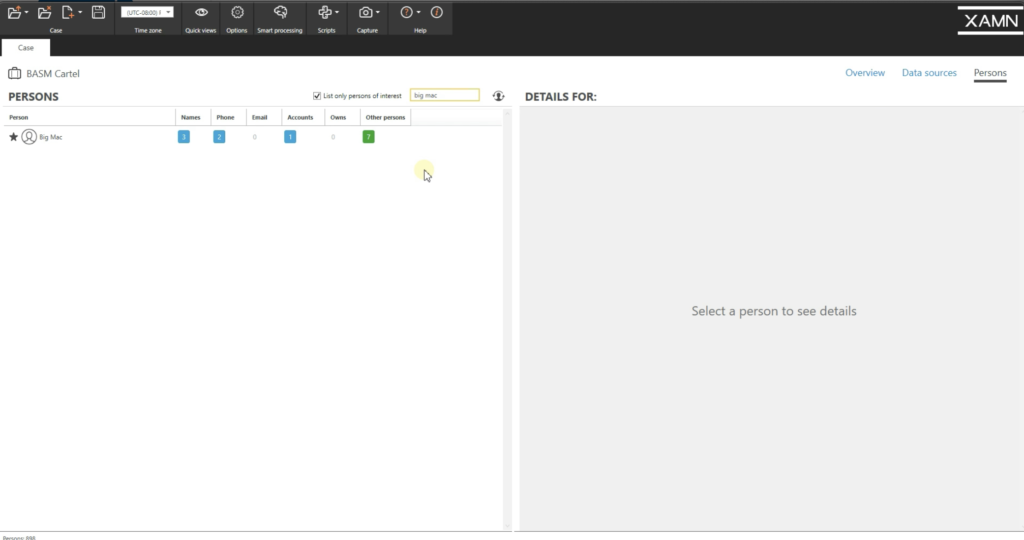
And if I erase this Big Mac here, now I run into Teddy and Large Mac every bit my persons of interest. So if I go back to my overview, open up all artifacts, I can open up a new filter with merely my participants. And you'll see here at the bottom now, I have Teddy Yaki and Large Mac, my two main suspects, and these numbers adjacent to them testify the number of artifacts associated with both of these people.
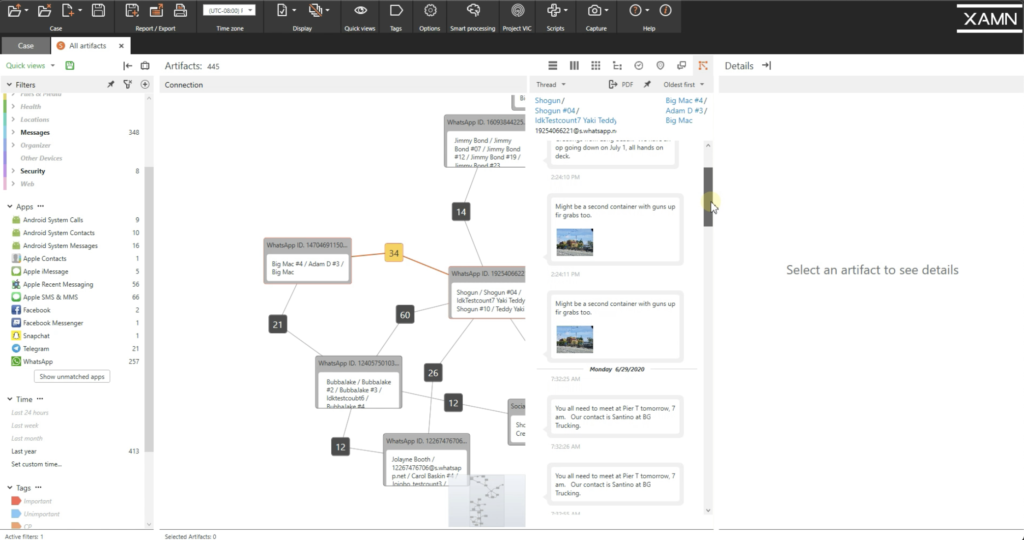
So if I click Teddy Yaki, you'll see all of the artifacts associated with Teddy Yaki, all these conversations I just pulled out. Same affair with Big Mac. I can run into that… all of his conversations equally well. And not only are these conversations through WhatsApp — here, you tin can run into WhatsApp — but it pulls out all conversations, whether it's WhatsApp — this is an Android message — more than WhatsApp… merely it'll pull information technology out from all of the different apps. If I highlight both of them, I could see both of their messages together. And if I expect in connections view, I can see if there's any connection between these people.
So in connections view, yous can now see how people are interlinked. I zoomed in on our connections view, and yous can see here, at that place's a chat, through WhatsApp, between Big Mac and Shogun, which is Teddy Yaki'due south nickname. You run into a number 34 between them. That means in that location's 34 letters that took place betwixt them, or information technology could be phone calls.
If I click on the 34, it'll tell me exactly what those artifacts are. And so it looks like it'southward mostly chats. Y'all can see the chat bubbles, the to and from, this is all between my 2 persons of involvement. That'south just one nice characteristic to help clean up your case and brand connections a lot easier in this jumbled mess of multiple extractions.
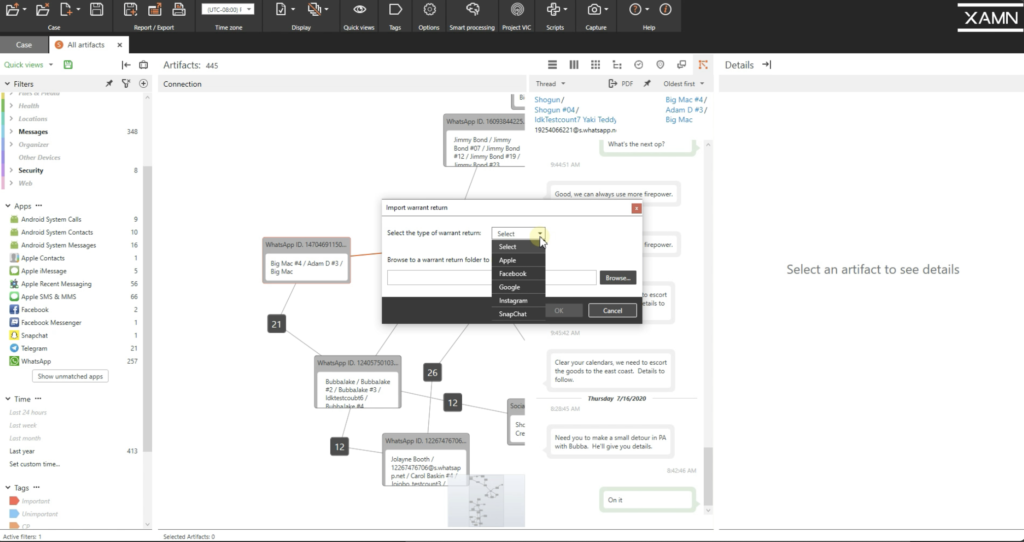
One final thing I want to point out in XAMN is our power to import records from other sources. Then if I become up here to the import tab, y'all can see we can import from other tools, like our main competitor, or nosotros could impart call data records. So whether information technology's from AT&T or Verizon, or whatever other service provider, we can import those records. Because as you know, these records can be difficult to read, and XAMN makes them hands read. If there'due south location information within those records it will map it out for you lot, and you lot tin can as well utilise the persons characteristic to assign names and even photos to the phone numbers y'all make it the CDRs. Because every bit you lot know, the CDRs don't include any names to go with the telephone numbers.
We can also import search warrant returns. And then we currently back up Apple, Facebook, Google, Instagram, and Snapchat. Many times, the service providers give you the information in formats that are extremely hard to open and read, because these providers only care almost being in compliance with their warrant. They don't actually care if you can read the data or non. So XAMN will automatically open the search warrant return for you, and brand them easy to read and to sift through that data.
Nosotros just recently assisted a Bay Area agency with their Google search warrant returns on a child exploitation case, where the suspect was a person of trust with easy admission to dozens and dozens of children. And so that imported information helped the detective assemble plenty evidence to execute a search warrant at the doubtable's residence, and he eventually arrested that person. Without XAMN that detective would still be trying to open these Google search warrant returns, and there'd be numerous children that would be in danger.
That was XAMN. And finally, I'd like to cover XEC. XEC is our management tool, used to manage your entire MSAB deployment. You can go along tabs on all of your equipment, your users, your licenses. Y'all can create reports, and these reports can exist user accounts to see their activity, or information technology could exist numbers and types of devices extracted. And you can even export these extractions to a key server with XEC. this can be especially useful if you're using some sort of analytics software, like Nuix or Penn link, because nosotros have full integration with those tools.
And so on the screen now is XEC Manager. Right now I'yard on the users screen, and yous can come across all the users within your deployment. You can see their status, when their terminal activeness was, what their experience level is. And you can edit that. Yous can generate reports from that. And you can add users here too.
This is our groups page. So y'all tin grouping your users into certain categories. Peradventure yous want to put all your detectives in one group and analysts in another group. Or yous could group them by skill level. The option is yours here as well.
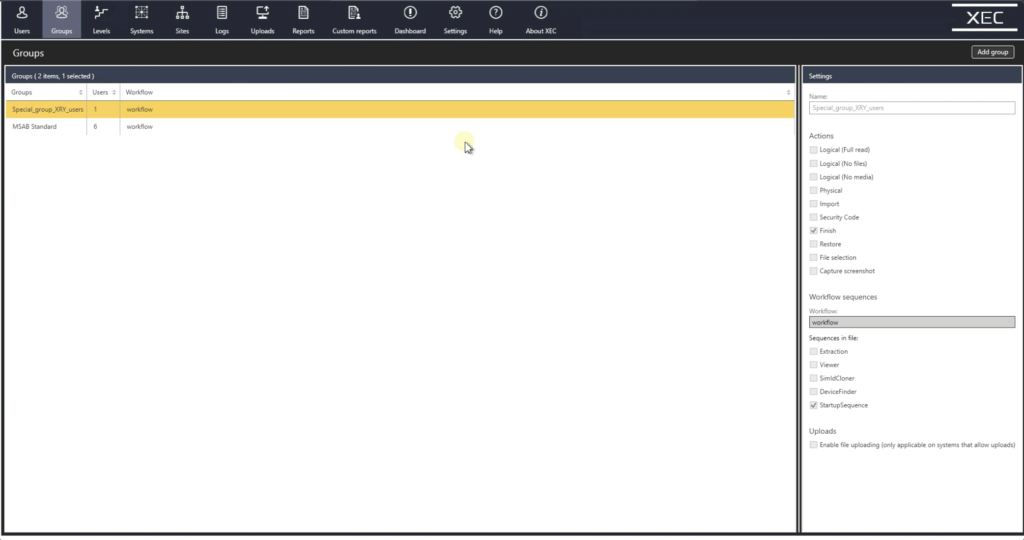
Levels. So this is a description of all the unlike user levels. And this is not fix in stone. Yous can customize these levels based on how yous'd like to fix upward your deployment.
The systems page will evidence every system within your deployment. And this exist peculiarly useful if you accept a very large department where your deployment is all over the place, or fifty-fifty a large task force, where y'all accept systems in several different locations. And from the systems, information technology tin encounter what type of system information technology is. Nosotros have kiosks, we have tablets, we have our regular office kits. You tin meet if it'due south online, yous tin can encounter what version number they're running, how much drive space they have.
And very important here is the licenses. You tin can run across if their licenses are electric current. If they're almost to expire, like this one here, or if it is expired, yous could actually update the licenses here all in one place.
Sites, you can group your sites together, maybe accept taskforce licenses in i place and maybe sexual assaults in another place, and high-tech crimes in another. Y'all tin create dissimilar groups for your sites. Your logs will show you all of the activity in your system, whether it is user activity or extraction activity, all of that will be hither in your logs. And if I create a range, it will add together activity.
Uploads. If you have XEC Export, you can have all of your extractions saved in a central server. And this is particularly useful if you're using analytics software, such as Penn link or Nuix, that mode all of your extractions are in one place and you can run analytics off of that. You tin can create reports, and I'll show you what types of information you go from those reports, and the custom dashboard. I volition show you that too. It's not ready on this i, merely I will bear witness you what data will be within your dashboard.
What you see hither are 2 sample reports from XEC manager. The reports tin prove yous a lot of useful information, whether information technology's amounts of devices extracted, or types of devices extracted, possibly you could see trends in what your officers are running into, or it could be user generated study, where yous want to encounter if a specific user is utilizing the product. Maybe they're not having success with the product. Maybe they've only used it once in the concluding three months, where another location is very busy and could use another license. You lot can redeploy that license to another user or another location. And so reports tin can assist y'all quickly run into the status of your deployment.
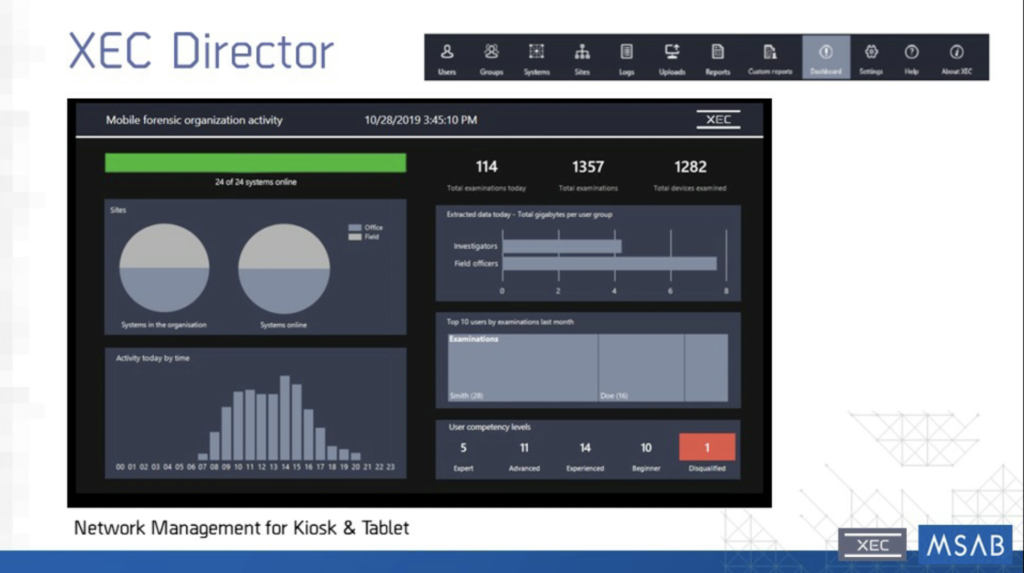
Now I'm showing you lot the dashboard of XEC Director. So with the dashboard, you could instantly see what'south going on with your deployment, whether it's how many devices are being extracted, types of devices being extracted, user activity. Yous can encounter it all speedily and easily with but the press of a button.
Give thanks you lot for your fourth dimension today. I know this was a lot of information covered in a short corporeality of time. My contact data is upwards on the screen, and you can get a agree of me anytime. And I'm also open up to whatsoever questions right now in the brusk amount of time we have left.
Source: https://www.forensicfocus.com/webinars/the-integrated-future-of-mobile-forensics/
0 Response to "Unplug Then Plug Back in It Starts Again Mobile Forensics"
Enviar um comentário